CertiK outlines three crypto exploits targeting DeFi users
A report published on January 11 details the most common honeypot schemes in DeFi and how to identify them through block explorers.

Share this article
Blockchain security firm CertiK listed three common ‘honeypot’ schemes created by exploiters to steal users’ crypto in decentralized finance (DeFi) in a report titled ‘Honeypot Scams’ published on January 11.
Honeypots are deceptive schemes targeting crypto investors and often lure victims with the promise of lucrative returns, only to trap their funds through different mechanisms. The alluring price charts with continuous green candles influence investors’ fear of missing out (FOMO), leading to impulsive buying. Once bought, these tokens become illiquid due to specific mechanisms preventing their sale.
The first mechanism is labeled by CertiK as ‘The Blacklist’, and its execution consists of preventing users from selling scam tokens through a lock inserted into the smart contract. The report gives an example by mentioning the ‘_snapshot list’ and ‘_snapshotApplied’ functions, which let users move tokens. Both of them must be set as ‘True’ in the smart contract, otherwise, the user will be blocked from transferring funds, acting as a ‘blacklist’.
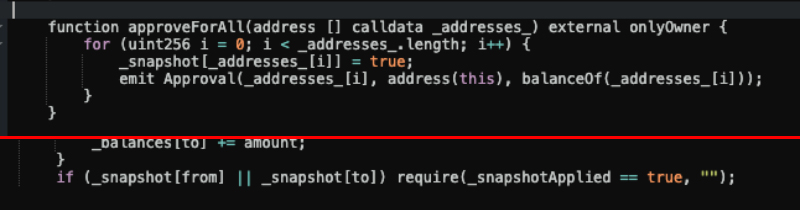
Although the blacklist command could be seen via a smart contract check, CertiK highlights that some blacklists are cleverly concealed within seemingly legitimate functions, trapping unwary investors.
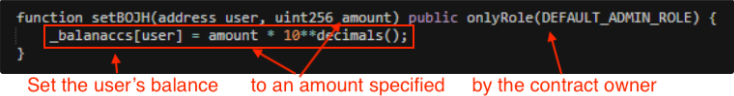
‘Balance Change’ is another common honeypot mechanism applied by scammers. This technique involves altering a user’s token balance to a nominal amount set by the scammer and it is only readable by the smart contract.
This means that block explorers like Etherscan won’t update the balance, and the user won’t be able to see that the token amount was reduced by a significant amount, usually just one token.
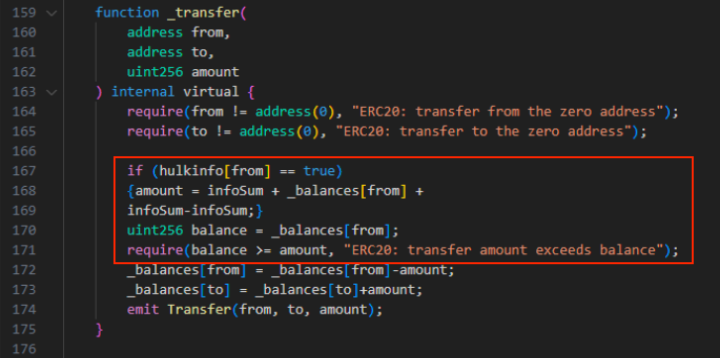
The last common tactic used by exploiters on DeFi projects’ smart contracts is the ‘Minimum Sell Amount’. Although the contract allows users to sell their tokens, they can only do so when selling above an unattainable threshold, effectively locking up their funds.
In this case, the user wouldn’t be able to sell even if the wallet has more tokens than the threshold set. This is because of the function ‘infosum’ used in this technique, which is considered on top of the amount set to be sold.
As an example, if a user buys 35,000 tokens from a project in which the smart contracts set the selling threshold to 34,000 using the ‘infosum’ function, the operation wouldn’t succeed. That’s because the user would have to sell 35,000 tokens plus the 34,000 set. In other words, the 34,000 extra tokens requirement could never be met.
The impact of honeypots
On top of the technical side of honeypot scams, exploiters also add a social layer to the scheme, mimicking reputable crypto projects to deceive investors. Moreover, bad actors devised a way to automate the creation of honeypots. CertiK’s report mentions a wallet responsible for creating scam contracts every 30 minutes over two months. In total, 979 contracts connected to this service were identified.
If an average of $60 was stolen, which is a fairly small amount compared to larger scams on DeFi, approximately $59,000 would be taken from users over two months. According to CertiK, this turns “vigilance and education” into an urgent matter in DeFi.
Share this article