
Shutterstock cover by amiak (edited by Mariia Kozyr)
Harpie Review: Can This On-Chain Firewall Solve Web3’s Security Problem?
Harpie is an on-chain Ethereum service designed to protect crypto users from various exploits.
Harpie’s on-chain firewall lets crypto users connect their Web3 wallets and create a safe transacting environment and protect themselves against crypto’s most common attack vectors.
Crypto’s Security Problem
As crypto and decentralized finance have risen in popularity over the last couple of years, so have cryptocurrency-related attacks, including targeted user thefts and protocol exploits. According to Chainalysis‘ mid-year crypto crime report, over $1.9 billion had been stolen in hacks of users and services from January through July 2022, up from just under $1.2 billion over the first seven months of 2021. And while most of the exploits have been protocol-related, many users have had their wallets drained thanks in part to the risks associated with using Web3 today.
For users who regularly interact with DeFi protocols and NFT marketplaces, transacting in Web3 can almost feel like playing Minesweeper in real life. Every transaction approval and on-chain interaction with a third-party application can potentially lead to wallet compromise and loss of funds. Unfortunately, there hasn’t been a simple or efficient solution to this problem so far. The most popular Web3 wallets, like MetaMask or Trust Wallet, do an abysmal job of conveying the nature of each on-chain interaction to their users. Instead of making each transaction clear, the default descriptions of most in-wallet transaction confirmations read like gibberish to most unsophisticated users, leaving them effectively blind to even the most basic security threats.
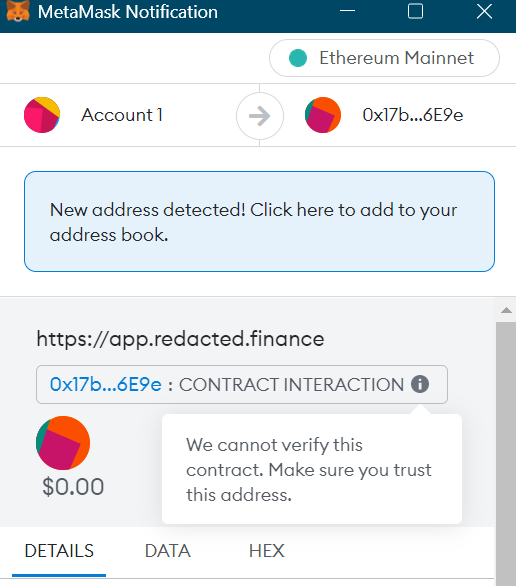
Beyond the usual protocol hacks, perhaps the most dangerous type of attacks affecting crypto users are so-called “approve spend” exploits that trick users into approving malicious transitions that allow the hackers to drain the users’ wallets. Another common way Web3 users lose their money is by having their private keys compromised, which typically involves users installing malicious software like keyloggers, storing their seed phrases in plain text on insecure devices, or falling for phishing scams.
Protecting against all of these attack vectors has always been possible, but it requires significant technical knowledge, sophistication, and sacrifices in user experience. Harpie is hoping to solve this problem.
What is Harpie?
Harpie is the first on-chain firewall solution that lets Ethereum users create a safe transacting environment by whitelisting a set of addresses and Web3 applications they deem safe. The service monitors connected wallets for pending suspicious or unpermitted transactions to stop them when they surface. When it detects a suspicious transaction, it immediately moves the user’s funds out of their wallet and into a safe, non-custodial vault, protecting the funds from potential theft.
Harpie does this by frontrunning malicious transactions by paying a higher gas fee. For example, suppose a hacker has somehow gotten hold of a user’s private keys or fooled them into approving a malicious spending transaction and tried to transfer funds from the victim’s wallet into his address. In that case, Harpie would detect the outgoing transaction from the victim’s wallet to an unapproved address, and automatically broadcast another transaction with a higher gas fee to move the target’s funds into a safe vault before the outgoing transaction is confirmed.
Ethereum validators prioritize transactions with the highest gas fees, which means they can pick up and confirm Harpie’s benevolent transactions before any attackers, thus saving users from theft.
After Harpie has intervened and moved the assets to a safe place, the user can withdraw them to a new uncompromised wallet for a flat fee of 0.01 ETH, regardless of the amount that was saved in the procedure.
How to Use Harpie
Users must connect their existing Web3 wallet to Harpie to use the service. They can do this by clicking the “Enter App” button in the top right corner of Harpie’s homepage and then clicking “Connect” inside the application. Users also need to confirm the connection inside their wallets separately to give Harpie permission to monitor their wallets and move funds from them in case of an incident.
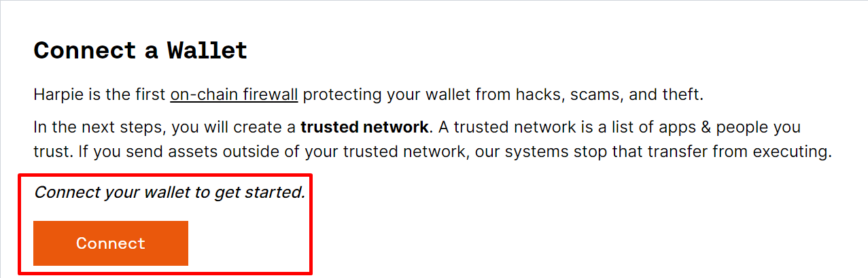
After connecting, users are asked to set up their “Trusted Network” of applications and addresses. These are applications and addresses the users deem safe and wish to exclude from the firewall, meaning Harpie won’t automatically block any transactions with them.
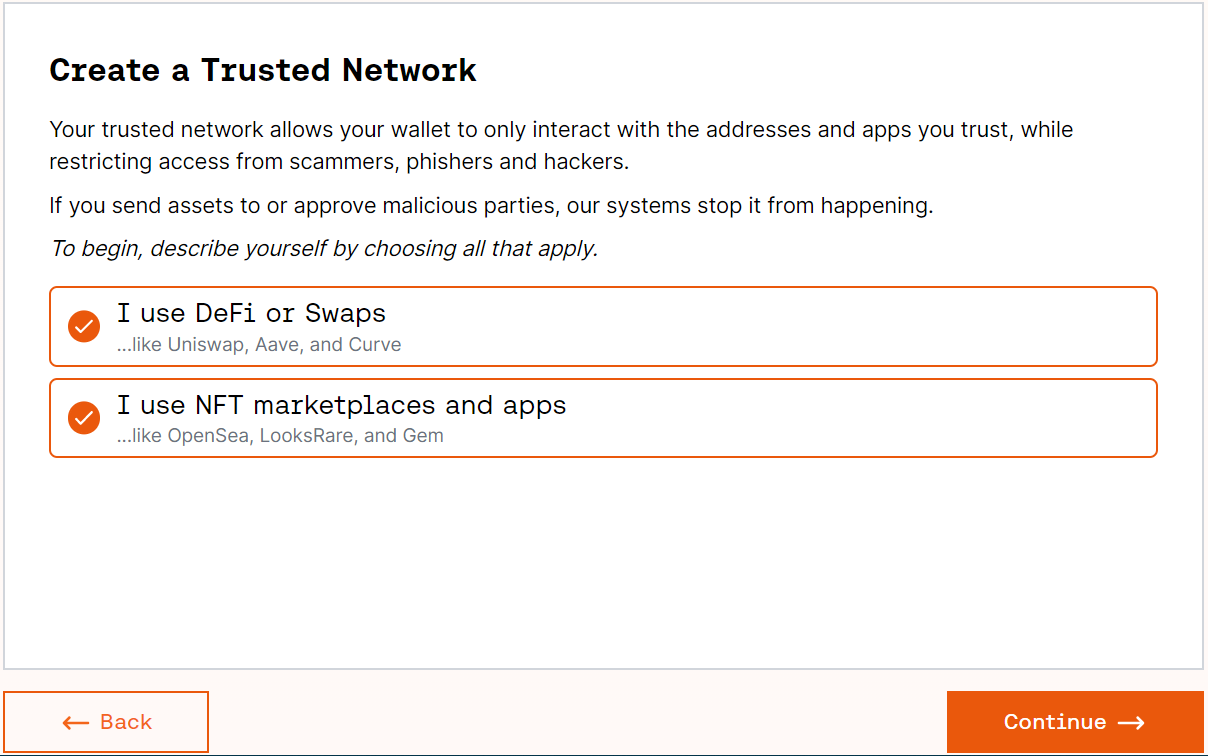
To do this, users can choose if they use DeFi applications, NFT marketplaces, or both and select their trusted network of applications from a preselected list of established protocols. All of the protocols that Harpie recommends by default have undergone extensive auditing, stood the test of time, and are generally considered secure, meaning users should feel safe about whitelisting all of them. After selecting the trusted set of applications, users must press “Continue” in the bottom right corner and sign the transaction inside their wallet.
Upon signing, Harpie will start integrating its firewall system with the user’s wallet, and after it’s finished, users will be directed to their dashboard. There, they can navigate to the “My Trusted Network” tab and add all the addresses they’re regularly interacting with under the “Friends” section. These may include their own personal wallets, their friends’ wallets, and the deposit addresses of the centralized exchanges they use.
Users must also permit Harpie to access their wallet’s funds to be able to move them to a secure vault in case of an attack. They can do this by clicking “Protect” for each asset in their dashboard’s “Protected Assets” section. If they can’t see all the assets they’re holding in their wallet, they can import them manually from the same dashboard section.
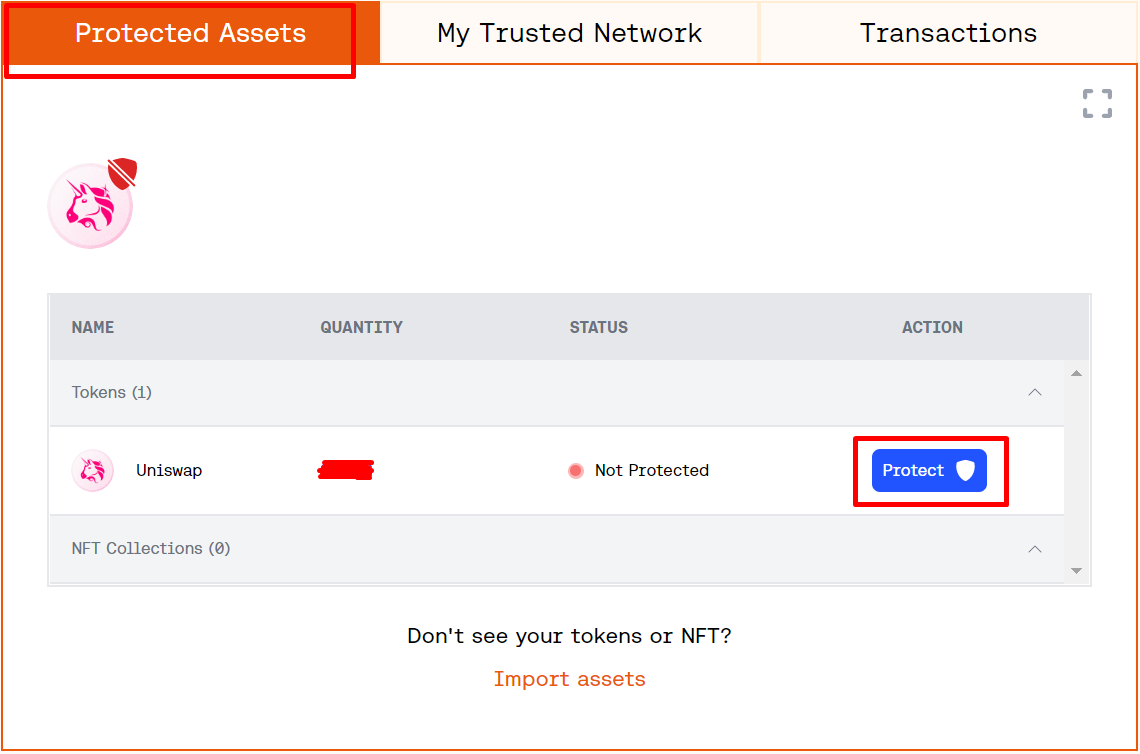
Clicking “Protect” for each asset is the most critical task for every user using Harpie. This is because whitelisting a trusted network of applications and addresses only tells Harpie what traffic to monitor, whereas permitting it to access the wallet’s funds is what actually allows it to intervene and move the assets to a safe place in case of an attack.
Finally, users need to set up a withdrawal address that will have the ability to retrieve the funds moved to the safe vault in case Harpie has intervened during a security breach. They can do this by clicking on the “Setup” button in the “Setup withdrawal address” section, entering the address they want to use for retrieving funds, clicking “Register,” and then approving the action with their wallet.
It’s important to clarify that Harpie can only protect users from losing assets they already have in their wallets. If users deposit or stake their assets on a third-party crypto protocol and the application gets hacked, Harpie won’t be able to do anything to protect the users’ funds.
Final Thoughts
While no single system or protocol can solve crypto’s security problem, Harpie’s on-chain firewall approach adds an essential layer of security to the daily operations of the more active Web3 users. Beyond protocol hacks and certain edge cases, Harpie can effectively protect users against almost common crypto exploits without severely impeding their user experience.
With that said, interacting with Web3 with Harpie’s firewall solution still introduces some inevitable hindrances from a user experience standpoint. For example, users may forget to whitelist their friend’s address or their own account on a centralized exchange and have their assets automatically moved to Harpie’s non-custodial vault after they attempt to make an intentional transfer. Beyond that, Harpie also doesn’t provide users with a simple way to revoke the firewall’s access. Once enabled, users need to use a third-party application like revoke.cash to revoke the access they’ve given to Harpie if they wish to opt-out of it.
Everything considered, Harpie provides a much-needed on-chain security layer that users currently can’t find anywhere else. While Harpie is not perfect today, its solution is a clear step in the right direction toward making Web3 safer for regular users.
Disclosure: At the time of writing, the author of this article owned ETH and several other cryptocurrencies.

 Earn with Nexo
Earn with Nexo