Ethereum Myth Busted: Apples To Oranges On 51 Percent Attacks

Share this article
Recently, Richard Gendal Brown, CTO of Corda, published an argument that Ethereum is not prepared for enterprise adoption because of the recent 51% attack on Ethereum Classic (ETC).
Brown’s argument is paraphrased as follows:
- The Ethereum network’s utility to enterprise blockchains rests in the ability of those consortia blockchains to ‘anchor’ their data in the public mainnet.
- By doing so, private blockchains can feel secure about the immutability and safety of their data if it’s regularly committed to a global, distributed, airtight blockchain.
- However, the recent successful 51% attack on Ethereum Classic demonstrates that the public Ethereum mainnet is not safe, and therefore enterprises should not trust Ethereum.
The vulnerabilities that led to the 51% attack against ETC cannot be replicated on the Ethereum network.
To conflate the two different technologies suggests either 1) a fundamental misunderstanding of blockchain technology, or 2) a marketing effort to capitalize on the confusion of the nuances of different blockchain systems to promote one’s own platform. Brown is a well-respected thought leader at Corda and in blockchain and enterprise DLT. Therefore, we will assume Brown saw a marketing opportunity to sow misunderstanding and doubt, and he took it.
Busting the Myth of Public Blockchains for Business: it’s time to talk about transaction finality. Why last week’s 51% attack demonstrates that Ethereum is not ready for business https://t.co/Ue7f4vHVwP
— Richard Gendal Brown (@gendal) January 14, 2019
A Quick Primer on 51% Attacks
A 51% attack is a type of attack performed on a proof of work blockchain to obstruct or change probabilistic finality – or, the moment at which an operation (block) is agreed to be complete and immutable. In proof of work, a majority of the miners on a blockchain are incentivized to act ‘honestly’ – which means they mine off the longest chain of blocks. If they don’t act honestly and continue mining off a different chain, they waste energy and money on mining blocks that will never be recognized by the rest of the network, so their block rewards are worthless.
A majority attack occurs when a single party (or coordinating group of parties) accumulates 51% of a blockchain network’s hashrate. To do this, they must expend energy to own that hashrate, after which they are able to build a chain of blocks that is longer than the one upon which the the rest of the network is building.
When the malicious actors release that longer chain to the network, the rest of the miners continue acting honestly – i.e. they start mining off that new chain. The issue is, of course, that the malicious actors built that chain themselves and could change the record of any transaction in the previous blocks they built. When they release the chain to the mainnet, their version of transactions would become the ‘truth.’
ETC is the largest blockchain by market cap to have been subject to a successful 51% attack, but other networks including Verge and Bitcoin Gold have experienced the same. In all these cases, the events were ‘double spend’ attacks targeted against centralized exchanges. Attackers would trade a coin for fiat currency on an exchange, then 51% attack the network and change the block history to show that they never traded those coins – meaning they’d be left with the fiat amount in their bank and those coins back in their exchange accounts.
This is what happened with ETC in early January 2019. An attacker double spent ~200,000 ETC [~$1.1 million USD] by changing the records of roughly 100 previously-confirmed blocks.
Ok, now to address Brown’s arguments:
Terminology: “Ethereum-style Blockchains”
Throughout the article, Brown uses ambiguous terms to categorize ETC and ETH under the same umbrella. He mentions “Ethereum-style blockchains,” “public blockchains such as Ethereum,” and “a high profile Ethereum network” when he’s discussing ETC and alluding to ETH.
Brown, however, never exactly defines what he means by “Ethereum-style” blockchains. If he just means public blockchains, then he believes ETC’s 51% attack means even BTC isn’t safe, even though BTC is widely regarded as the most secure network based off age alone, and would require an estimated ~$1.5 billion to pull off a 51% attack (if enough computing power could even be accumulated, which is unlikely).
Perhaps Brown means blockchains that use PoW and ethash to achieve finality. Or perhaps, more specifically, he means ASIC-resistant blockchains that could allow a potential hacker to gather GPU power on the open market to direct towards an attack. Either of these categorizations would require further delineation based off hashrate, difficulty, and available GPU power.
Unfortunately, Brown never clarifies what he means by “Ethereum-style” blockchains, further suggesting he seeks only to associate ETH and ETC in people’s’ minds when no such association is appropriate. In short, there is no such thing as an “Ethereum-style” blockchain, and most definitely not with respect to levels of security.. (Given that Brown’s previous writing has historically been admirably concrete and unambiguous, one could surmise the obfuscation is deliberate in this instance).
Public Blockchains: ETH ≠ ETC
Ethereum and Ethereum Classic became separate blockchains in May 2016, after the DAO hack that caused the community to fork the Ethereum chain to create ETH and ETC. The large majority of the community supported Ethereum, with a few die-hard purists staying committed to ETC.
Though ETC has remained in the top 20 coins by market cap since, not too much else has happened on the network. StateOfTheDapps and DappRadar list 0 dapps built on ETC. In fact, the 51% attack is perhaps the most noteworthy event to have happened to ETC since the DAO fork in 2016.
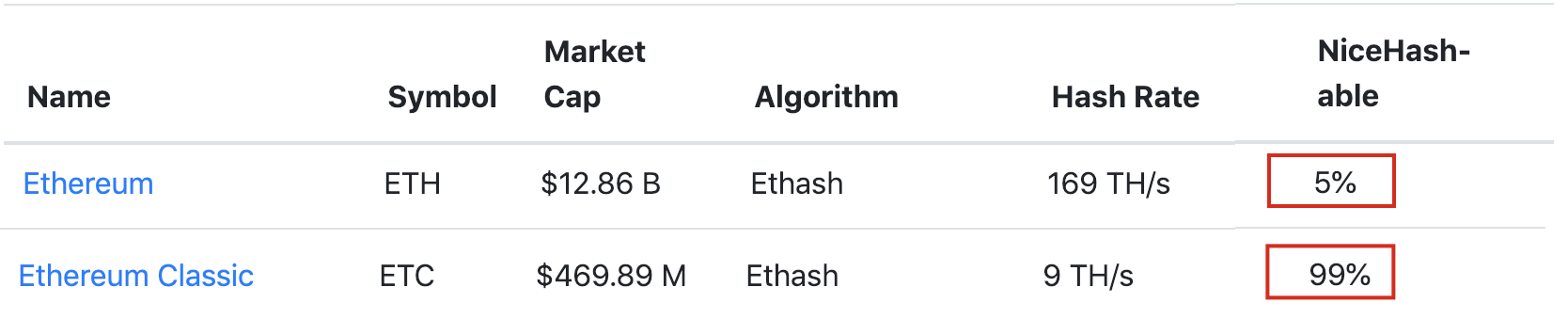
The sparse network of miners supporting ETC means the network has been maintained at a low hashrate and difficulty. A consistent block explorer like etherscan does not exist for ETC, but existing data does show a hashrate of ~8k and a difficulty of ~121 TH, compared to Ethereum’s hashrate of 181k and difficulty of 2,600 TH.
Less than $5,000 per hour was required to launch a 51% attack on Ethereum Classic. Most importantly, 99% of that hashing power could be rented on the open market on a site like NiceHash. Meaning the attacker did not have to spend much capital at all on GPUs or hardware to launch the attack successfully. Instead, all they needed to do was go online and rent available hashing power from mining sites.
Ethereum, on the other hand, has 23x+ the hashrate and 21x+ the difficulty of ETC. And only 5% of the hashing power required to launch a 51% attack on Ethereum is available to rent online on a site like NiceHash. The remaining hashing power required would have to be generated from GPU and CPU hardware purchased on the open market, a capital investment in the hundreds of millions. The additional few hundred thousand in electricity costs and the estimated $85,000/hour to actually launch the attack is just icing on top.
 Ethereum Classic succumbed to a 51% attack not because it was a PoW chain, and not because it was public, and not because it was originally forked from Ethereum. It succumbed because it is an extremely weak public, proof of work blockchain and it was cheap to attack, just as Verge and Bitcoin Gold were.
Ethereum Classic succumbed to a 51% attack not because it was a PoW chain, and not because it was public, and not because it was originally forked from Ethereum. It succumbed because it is an extremely weak public, proof of work blockchain and it was cheap to attack, just as Verge and Bitcoin Gold were.Ethereum, on the other hand, is a world away from ETC. The economics of attacking ETH are orders of magnitude more than ETC, and it’s very possible the amount of power from GPUs needed to launch an attack simply is not available to rent in the world.
Ethereum Classic cannot be legitimately compared to Ethereum. As it relates to their respective levels of security, the word “Ethereum” is just about the only thing they share. The 51% attack on ETC is only a demonstration of the weakness of low-hashrate, low-difficulty, sparse network, proof of work chains. It does not demonstrate in any way that Ethereum is unsafe to transact on, for individuals or for enterprises.
Private Enterprise Blockchains
Brown argues that private, consortia blockchains cannot be safe if anchored in public blockchains, but glosses over the actual mechanics of a private, enterprise ethereum platform. Instead, he leads the reader to believe that if a public blockchain could suffer a 51% attack, then a private chain built off the same technology could as well.
In the previous section, we demonstrated that ETC’s 51% attack has no implications for the security of the Ethereum public mainchain. However, even if it did (which, again, it does not), a 51% attack on the public mainchain would be impossible to replicate on a private consortia blockchain, unlike what Brown suggests. 51% attacks are only possible on proof of work blockchains. No enterprise ethereum consortium is using proof of work to reach finality. Rather, they are using proof of authority, RAFT, or IBFT. All of these methods provide immediate (or almost immediate) finality.
Brown deliberately conflates settlement finality and anchoring. A private enterprise chain already has internal settlement finality through RAFT, IBFT, or PoA. The anchoring of a private chain in the public Ethereum mainchain serves to create a public record of that already-established private settlement. If the public anchor was compromised by a 51% attack (which, to reiterate yet again, it cannot be), then the private chain could establish periodic new anchoring events.
Brown’s main argument on this point is: “If your enterprise blockchain needs settlement finality but the chain into which it is ‘anchored’ provides only probabilistic finality, when is it safe to tell a user of the private chain their transaction has been confirmed?”
The key mistake here is the word “only” – suggesting probabilistic finality is inherently weak. It is true Ethereum relies on probabilistic finality as a public PoW chain. On a network with a high hashrate, however, probabilistic finality is extremely reliable. ETC’s probabilistic finality was not reliable, as its hashrate was 23x+ less than Ethereum’s at the time of the attack.
It is also important to note consortium/private chains do not use probabilistic finality – a benefit with respect to finality immediacy, but leaving it vulnerable to manipulation from the small group that controls it. By anchoring private chains in the Ethereum public mainnet, enterprises do benefit from the best of both, despite what Brown seeks to misconstrue.
And as a final note, Proof of Stake – which offers true finality – is just down the road for Ethereum.
In short, a 51% attack can only happen with proof of work. Consortium enterprise Ethereum blockchains do not use proof of work on their chain. Brown leaves out this crucial detail, leaving room for people to conflate public mainchain finality with private chain finality.
51% Attacks: Conclusion
It is easiest to summarize the points above as follows:
- ETH is not similar to ETC. There is no “family” of blockchains that are uniquely susceptible to 51% attacks.
- ETC was successfully attacked because of a low hashrate and the availability of GPU mining power on the open market. The hashrate of ETH is higher than ETC many times over, and it’s likely the amount of power needed to launch a successful 51% attack simply isn’t available on the open market.
- A 51% attack is only possible on proof of work blockchains. Enterprises that use Ethereum for consortium blockchains do not use proof of work to reach finality. Instead, they use instant-finality solutions like RAFT, IBFT, or proof of authority.
- Ethereum is the only ecosystem with both a public blockchain community and an enterprise blockchain community. Anchoring to the public blockchain is a significant additive layer on top of a consortium blockchain. The fact that the Ethereum ecosystem is pioneering the connectivity between enterprise and public is a unique strength.
To conclude, Brown’s argument does not stand. It is not a matter of opinion or looking at the data in a particular way; it is simply untrue.
The 51% attack on ETC demonstrates the weakness of ETC and…that’s it. At most, it could be considered a sign of vulnerability for PoW chains with low hashrate and sparse node networks. But Ethereum does not belong to that group. It is safe, it is secure, and it is not going anywhere.
There are a handful of strong blockchain and DLT solutions for the enterprise space. Ethereum, Hyperledger Fabric, and Corda are all examples of solutions offering businesses more efficient and secure ways to coordinate and transact across their networks. Despite Brown’s desire to paint the ecosystem as competitive and limited, there is actually a huge abundance of growth opportunities in both the public and private blockchain and DLT realms. Ethereum can be applied safely and securely to both, and will continue to be used for public and private enterprise purposes alike.
Further, the benefits for private blockchain networks of being able to link to and anchor in an accessible, public chain seem to be clear and exciting to most people other than Brown. As he is aware, blockchain can help industries such as financial services operate more efficiently, for example, helping to settle transactions more quickly. But they should also offer the ability to connect with other networks, services and users, comply with legal regulations, and avoid collusion and unenforceability that can manifest in a smaller network.
Even IBM and Fabric have partnered with public blockchain Stellar for easier access to a public payments network. Ernst & Young is developing on the Ethereum public network working to make private transactions and permissioned networks possible on the mainchain itself, using advanced privacy techniques around ZK-Snarks.
It seems Brown’s Corda is the only solution unaware of the potential of private, permissioned chains interoperating with a public chain. As ConsenSys’ John Wolpert writes, a public root chain that is being scaled up will help to avoid “extranet-like” heavy lifting of standing up dedicated infrastructure every time you need to do something confidential between parties that may need to interoperate with other confidential business logic between other parties or with the public.
The Ethereum community at large stands for transparency and robust internal and external discussion, criticism, and suggestions. Articles like Brown’s – i.e. questions about Ethereum from outside the network – are crucial for continued blockchain growth and the community welcomes them.
We do not, however, stand for deliberate obfuscation meant to exploit confusion about blockchain technology among early adopters.
Clark Thompson leads ConsenSys’ global solutions architecture based out of Brooklyn, NY, building a team of top solution architects to support ideation, design and blueprint development on Ethereum and blockchain generally. Clark’s area of expertise is financial systems, with a deep background in transaction processing, clearing and settlement automation, and business architecture process and methodology across brokerage, investment management and private wealth.
Crypto Briefing does not accept any payment or financial benefit from expert guest authors.
If you are a blockchain expert with an interest in sharing your knowledge and experience, please contact our Managing Editor, Jon Rice, via email at editor AT cryptobriefing.com
Share this article
