
Princeton Researchers Say SIM Swapping Is a Major Problem
80% of simulated attacks were successful.
Researchers at Princeton University have demonstrated that five major phone carriers are highly vulnerable to SIM swapping attacks.
The team revealed the results of their experiment in a draft paper published Jan. 10. They also surveyed over 150 websites and determined whether user accounts could be accessed through such an attack.
Phone Carriers Are Not Secure
SIM swapping is “low-tech but devastating,” according to Arvind Narayana, an author on the paper.
As Narayana explains, attackers can contact a phone carrier, impersonate their victim, and transfer the victim’s service to their own SIM card. This allows the attacker to intercept verification codes through SMS and access the victims’ website accounts.
Princeton researchers attempted 50 SIM swaps by creating simulated identities and persuading carriers to reassign each account to a new SIM card. All 10 swaps involving AT&T, T-Mobile, and Verizon accounts were successful. Six Tracfone swaps were successful, and three US Mobile swaps succeeded. 39 of 50 attempts were successful overall.
The team additionally noted that AT&T, Tracfone, and US Mobile revealed personal data without authenticating the caller—including billing addresses, activation dates, and payment dates. Though that information alone does not guarantee a successful SIM swap, it could help attackers correctly guess the answers to security questions.
Researchers stated that they followed responsible disclosure procedures and submitted their findings to all five phone carriers. They also notified CTIA, a wireless communications trade agency.
So far, only T-Mobile has explicitly updated its security practices, but it is possible that other carriers have done so as well.
Crypto Exchanges Have Mixed Security
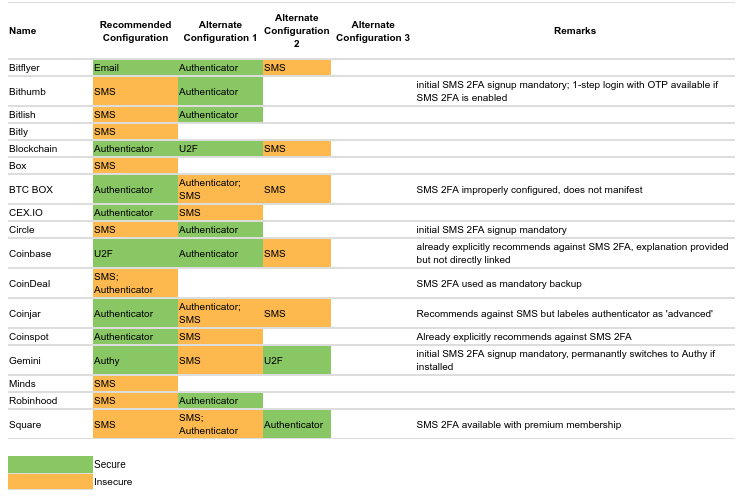
SIM swaps do not necessarily give attackers access to victims’ online accounts. As such, researchers assessed 156 websites to determine whether they were secure. They found that 83 sites were “insecure,” or accessible with a password and SMS verification. 17 sites were “doubly insecure,” or accessible with SMS verification alone.
The researchers included several cryptocurrency exchanges, online wallets, and crypto-related websites in their survey too.
Most of these sites offer secure two-factor authentication setups that do not rely on SMS verification. However, many crypto websites offer insecure account configurations, as seen below:
Why Crypto Accounts Are Targeted
SIM swapping and SMS verification can be used to target any sort of account, including bank accounts and social media accounts.
However, crypto exchange accounts are also quite profitable. Over ten cases of crypto theft related to SIM swapping have been reported in the past year, cumulating in tens of millions of dollars in stolen funds.
Sometimes, attackers operate serially. One particularly high-profile attacker, Joel Ortiz, stole more than $5 million of cryptocurrency in 2018. There are also plenty of big targets: Sean Coonce, the engineering manager of BitGo, lost $100,000 in a SIM swap attack that targeted his personal Coinbase account in May 2019.
Change might be on the way, however. Victims of SIM swapping have highlighted the issue by suing AT&T over negligent security practices.
Lawmakers are taking an interest as well: U.S. Congress asked the FCC to introduce protections against SIM swapping this week. But for now, individual security practices are the only true preventative measure.

 Earn with Nexo
Earn with Nexo