Poly Network Hacker Starts Returning $600M Loot
The hacker has returned over $2 million so far on Polygon and Binance Smart Chain.

Share this article
The hacker behind yesterday’s $600 million Poly Network exploit has started to return the stolen funds.
Poly Network Hacker Returns Funds
It seems the Poly Network hacker has had a change of heart.
The perpetrator behind the biggest DeFi attack to date has started to return the stolen funds, on-chain data shows.
The reversal comes less than 24 hours after the hacker took over $600 million across Ethereum mainnet, Binance Smart Chain, and Polygon.
In the hours following the attack, the hacker started communicating with onlookers through notes attached to transactions on the Ethereum network. In the notes, the hacker jokingly put forward the idea of creating a new token and letting the holders decide where the stolen funds should go.
My guy, just stop and turn yourself in already pic.twitter.com/wqdnui2azl
— Zach Rynes | CLG (@ChainLinkGod) August 10, 2021
However, the hacker’s most recent messages declared that they were “ready to return the fund,” prompting Poly Network to create a set of multisig wallets where the hacker could deposit the stolen funds.
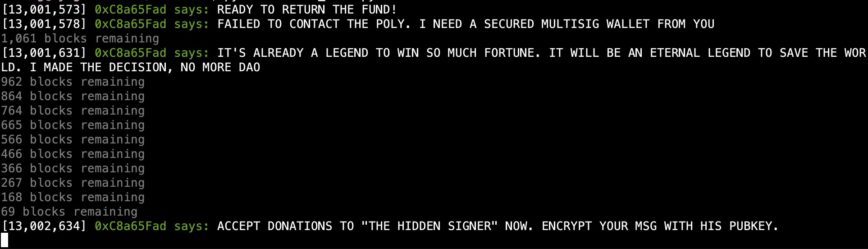
Before starting to return the funds, the hacker created a new token called “The hacker is ready to surrender” and sent it to Poly Network’s wallet. The hacker then started transferring USDC to the same wallet over three transactions totaling $1.0101 million. They also sent $1.1 million worth of the Binance-peg Bitcoin token BTCB via Binance Smart Chain, along with $2 million worth of Shiba Inu and $600,000 in stablecoins on Ethereum.
Although only around $4.7 million has been returned so far, it indicates that the hacker wants to make Poly Network whole again. The decision to return the funds may also be due to the blockchain security firm SlowMist identifying key information about the hacker, such as an email address, IP information, and device fingerprint. Additionally, the funds used to conduct the hack have been traced to the Hoo exchange, further compromising the hacker’s identity.
Update: This article has been updated to include additional funds returned by the hacker.
Disclaimer: At the time of writing this feature, the author owned BTC and ETH.
Share this article
