Sentinel Protocol ICO Review And UPP Token Analysis

Share this article
Sentinel Protocol ICO Overview (UPP Token)
The Sentinel Protocol ICO and UPP Token sale offer a product to address the pressing need for enhanced security in the crypto space. Sentinel Protocol refer to this product as the Security Intelligence Platform for Blockchain (SIPB). The SIPB is designed to provide both proactive and reactive solutions to threats via analysis of previous attack patterns, prediction of future attacks and deployment of prevention measures.
Sentinel Protocol ICO Value Proposition
The Sentinel Protocol team have designed their product for two purposes: to safeguard individual crypto holders, and to protect larger institutions like exchanges. All security services are provisioned through an integrated “Security Wallet”, otherwise known as the S-Wallet. The architecture of the entire system is comprised of the four following components:
- Security Wallet (S-Wallet)
- Threat reputation database (TRDB)
- The Sentinels
- Interactive Cooperation Framework (ICF)
S-Wallet: The S-Wallet is an end user software program. The function of the S-Wallet could be described as an antivirus software for cryptocurrency. However, a fundamental difference is that antivirus software responds to new threats by continually receiving updates via a centralized server for all new known signatures.
This approach makes it difficult to respond to unknown threats. S-wallet leverages access to a collective database of intelligence (TRDB) in conjunction with machine learning to generate a proactive response based on threat tendencies, patterns and history. Leveraging the collective intelligence of the TRDB, S-wallet provides the following basic services:
-
- Cryptocurrency wallet address filtering
- URL/URI filtering
- Data filtering
- Fraud Detection System
TRDB: The Threat Reputation Database comprises a collective source of information contributed by security experts and vendors on threats. Through the utilization of collective intelligence, TRDB will collect hacker wallet addresses, malicious URL/URIs, phishing addresses, malware hashes etc.
TRDB is only updated by security experts in order to reduce errors. End users can also participate in data submission via two methods: auto reporting and manual reporting. By enabling auto reporting, unknown threats that are detected from the S-Wallet will enter the database. Manual reporting allows users to report risk information which is then validated by the community.
The TRDB will be provided as an API, so any individual or organization (e.g. wallets, exchanges, security vendors) can submit a query before users conduct a transaction as an added measure of security.
The Sentinels: Sentinel Protocol introduces a human component to the system called Sentinels. The Uppsala Foundation aim to encourage cyber security experts around the world to become Sentinels and utilize their knowledge toward the betterment of the system.
The Sentinels will be comprised of both individual security experts and organizations who: 1) Validate hacking claims and trace the attackers 2) Analyze the root cause of a threat and update information via the TRDB 3) Contribute to the TRDB to help ensure it accurately reflects the most up-to-date security research and analysis.
Interactive Cooperation Framework (ICF): Sentinels and end users both interact with Sentinel Protocol via the Interactive Cooperation Framework (ICF), otherwise known as Sentinel Portal. Users report hacking incidents via the Sentinel Portal.
The Sentinel Portal also provides a dashboard for Sentinels to interact with and validate information based on user activities via root cause analysis, incident response, and macro-level statistical insights. Sentinels will earn Sentinel Points (SP) according to their level of contribution to the system and staking toward their reputation, which can be redeemed for the native currency of the platform.
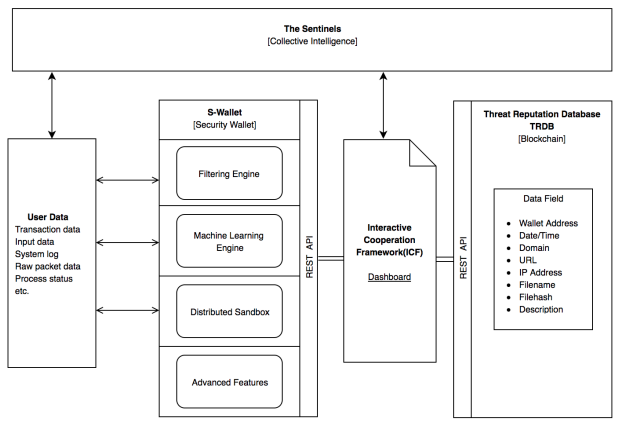
Architecture of SIPB from Whitepaper
Uppsala Token (UPP) is used to purchase services provided by the SIPB, such as advanced threat protection features offered on the S-Wallet. Basic features such as ETH address assessments do not require UPP.
UPP also can be used to purchase detailed cyber forensics, vulnerability assessments, and other related services offered by Sentinel Protocol. UPP are not directly awarded to Sentinels for their contributions. Instead, Sentinels are rewarded with Sentinel Points (SP). Sentinel Points allow participants to stake value on the reputation system and also exchange directly for UPP. Anyone can purchase UPP, but SP must be earned.
Sentinel Protocol ICO Team
Patrick Kim is the Founder and CEO of Sentinel Protocol. He has 10 years of experience in the cyber security industry. His previous work experience includes positions with Cisco, Palo Alto Networks and Darktrace, a leading cyber security company that develops machine learning products.
HM Park is Co-founder and Head of Operations. HM has been in the tech world for the last 10 years. His last two positions before joining Sentinel Protocol were both as Account Manager for Darktrace and F5 Networks.
John Kirch serves as Chief Evangelist and has a long track record of success in both finance and cyber security. John served first as a Regional Country Manager and then Regional Director at Darktrace over a period of 3 years. He has previous leadership experience as Director of DNS-based cloud security solutions company, Nominum, and served 5 years as VP of Asia-Pacific/President of Japan for Penta Security Systems.
The remainder of the team include core developers Dayeol Lee and Guo Feng. Dayeol Lee holds a PhD in Computer Science from UC Berkeley, and Guo Feng boasts 13 years of experience with computer engineering. Head of Threat Intelligence, Michael Zhou, has 3 years of experience in Threat Analysis and Head of Security Operations, Narong Chong, has 10 years of experience in computer engineering. Head of Marketing, Karly Choi, has held previous positions as both Marketing Manager and Marketing Director with tech companies in Korea and the US. Head of Product, Min Wu Koo, has 8 years of experience in business development and sales.
Additional information on the team can be found here.
Sentinel Protocol ICO Strengths and Opportunities
The team are already underway with product development and have completed a prototype. A demonstration of the prototype from the ICON summit can be viewed here. The beta version of the SIPB is scheduled for release in June, with Mainnet launch in July. While the final version of the SIPB that includes all features won’t be available until early 2019, it’s promising to see headway on the main components of the product.
Sentinel Protocol ICO has formed several partnerships with exchanges and wallets which will integrate the TRDB for querying addresses. By querying the database, they contribute new information to the system and receive a security assessment in return. The first exchange Sentinel Protocol has partnered with for integration of the TRDB is Kyber Network. In addition, Sentinel Protocol has formed partnerships with the largest wallets in China and Korea: imToken and Coinmanager. These partnerships will also include integration of the TRDB.
Sentinel Protocol ICO Weaknesses and Threats
Sentinel Protocol depends on participation from actual people to deliver the core value proposition of the product. Specifically speaking, the product depends on the participation of cyber security experts.
To this accord, a Pre-Sentinel recruitment program was conducted to begin the onboarding process. While it’s promising to see recruitment efforts are already underway, the team have indicated their strategy will rely heavily on B2B partnerships for growing the number of Sentinels in the ecosystem.
At this stage, the Sentinel Protocol ICO team has yet to establish any partnerships that would guarantee the number of Sentinels required for a sustained scaling effort. It also remains uncertain to what extent incentivization of enterprise partners through earning Sentinel Points and UPP will prove viable.
End user adoption of the product is dependent on the active participation of Sentinels for functionality, so this point is critical. As Sentinel Protocol moves forward, we will pay close attention to any developments on this front.
The Verdict on Sentinel Protocol
The crypto community recently received a harsh wake-up call with the hack of a high-profile crypto influencer. The Founder of Sentinel Protocol, a cyber security expert himself, was also the victim of a hack resulting in the loss of thousands of ETH. His experience is what ultimately lead to the birth of this project.
It’s beyond doubt a comprehensive security protocol is essential for the cryptospace, and the team of cyber security experts behind Sentinel Protocol are building one potential solution that could very well meet this need. With a product to develop and an ecosystem to grow, Sentinel Protocol still have a ways to go.
Nonetheless, the strength of the team, community support and partnerships to date are all indicators of strong potential. We rate the Sentinel Protocol ICO in our Top 10%.
Learn more about the Sentinel Protocol ICO from our Telegram Community by clicking here.
We have rated hundreds of projects to unearth ICOs in which members of our team intend to invest.
We won’t often go into further depth on projects that we don’t consider as candidates for our investments after the initial rating process, which is why you will usually see our stamp on our detailed ICO reviews – they are the best we have found. However, on occasion, we might also rate a well-hyped project that does not meet our personal investing criteria.
The Crypto Briefing Top 10 stamp is awarded to ICO projects that we rate in the top 10% of all projects.
SENTINEL PROTOCOL ICO REVIEW SCORES
SUMMARY
The Sentinel Protocol ICO (UPP Token) grasps the thorny issue of cryptocurrency security, with a view to shaking out the bad actors who stalk the crypto world. A partnership with Kyber Network illustrates that the existing product has a strong foundation, and the experienced team instill confidence that the technology will be strong. However, just like any two-sided market that depends on mass adoption for customer value, we have some concerns about the scalability of the venture. We hope they are unfounded.
Founding Team……………………….8.6
Product…………………………………..6.4
Token Utility…………………………..7.5
Market…………………………………..5.2
Competition…………………………..8.1
Timing……………………………………9.8
Progress To Date……………………5.5
Community Support & Hype…..6.8
Price & Token Distribution……..8.3
Communication……………………..10.0
FINAL SCORE……………………….7.6
UPSIDES
- Team are industry experts in cyber security
- Have launched and demonstrated prototype
- First-mover advantage
DOWNSIDES
- Incentivizing participation remains a critical question
- Product development still in early stages
Today’s Date: 4/18/18
Project Name: Sentinel Protocol
Token Symbol: UPP
Website: https://sentinelprotocol.io/
White Paper: https://sentinelprotocol.io/whitepaper/
Crowdsale Hard Cap: $22 million
Initial Supply: 500 million
Token Distribution: 60% to public, 15% for business development, 15% for Uppsala Foundation, 8% for unforeseen business activities, and 2% for advisors
Price per Token: 1 UPP = $0.08 USD
Initial Market Cap (at crowdsale price): $40 million
Accepted Payments: ETH
Countries Excluded: China, US
Bonus Structure: N/A
Presale Terms: N/A
Whitelist: April 25 Crowdsale KYC registration
Important Dates:
- April 25 – May 5: Crowdsale KYC registration
- May 10: Crowdsale KYC results released
- May 11: Crowdsale begins
Expected Token Release: TBA
Additional Information: https://t.me/sentinelprotocol
ICO Review Disclaimer
The team at Crypto Briefing analyzes an initial coin offering (ICO) against ten criteria, as shown above. These criteria are not, however, weighted evenly – our proprietary rating system attributes different degrees of importance to each of the criteria, based on our experience of how directly they can lead to the success of the ICO in question, and its investors.
Crypto Briefing provides general information about cryptocurrency news, ICOs, and blockchain technology. The information on this website (including any websites or files that may be linked or otherwise accessed through this website) is provided solely as general information to the public. We do not give personalized investment advice or other financial advice.
Decentral Media LLC, the publisher of Crypto Briefing, is not an investment advisor and does not offer or provide investment advice or other financial advice. Accordingly, nothing on this website constitutes, or should be relied on as, investment advice or financial advice of any kind. Specifically, none of the information on this website constitutes, or should be relied on as, a suggestion, offer, or other solicitation to engage in, or refrain from engaging in, any purchase, sale, or any other any investment-related activity with respect to any ICO or other transaction.
The information on or accessed through this website is obtained from independent sources we believe to be accurate and reliable, but Decentral Media LLC makes no representation or warranty as to the timeliness, completeness, or accuracy of any information on or accessed through this website. Decentral Media LLC expressly disclaims any and all responsibility from any loss or damage of any kind whatsoever arising directly or indirectly from reliance on any information on or accessed through this website, any error, omission, or inaccuracy in any such information, or any action or inaction resulting therefrom.
Cryptocurrencies and blockchain are emerging technologies that carry inherent risks of high volatility, and ICOs can be highly speculative and offer few – if any – guarantees. You should never make an investment decision on an ICO or other investment based solely on the information on this website, and you should never interpret or otherwise rely on any of the information on this website as investment advice. We strongly recommend that you consult a licensed investment advisor or other qualified financial professional of your choosing if you are seeking investment advice on an ICO or other investment.
See full terms and conditions for more.
Founding Team
This category accounts for the leaders, developers, and advisors.
Poor quality, weak, or inexperienced leadership can doom a project from the outset. Advisors who serve only to pad their own resumes and who have ill-defined roles can be concerning. But great leadership, with relevant industry experience and contacts, can make the difference between a successful and profitable ICO, and a flub.
If you don’t have a team willing and able to build the thing, it won’t matter who is at the helm. Good talent is hard to find. Developer profiles should be scrutinized to ensure that they have a proven history of working in a field where they should be able to succeed.
Product
What is the technology behind this ICO, what product are they creating, and is it new, innovative, different – and needed?
The IOTA project is a spectacular example of engineers run amok. The technology described or in use must be maintainable, achievable, and realistic, otherwise the risk of it never coming into existence is incredibly high.
Token Utility
Tokens which have no actual use case are probably the worst off, although speculation can still make them have some form of value.
The best tokens we review are the ones that have a forced use case – you must have this token to play in some game that you will probably desire to play in. The very best utility tokens are the ones which put the token holder in the position of supplying tokens to businesses who would be able to effectively make use of the platforms in question.
Market
There doesn’t have to be a market in order for an ICO to score well in this category – but if it intends to create one, the argument has to be extremely compelling.
If there is an existing market, questions here involve whether it is ripe for disruption, whether the technology enables something better, cheaper, or faster (for example) than existing solutions, and whether the market is historically amenable to new ideas.
Competition
Most ideas have several implementations. If there are others in the same field, the analyst needs to ensure that the others don’t have obvious advantages over the company in question.
Moreover, this is the place where the analyst should identify any potential weaknesses in the company’s position moving forward. For instance, a fundamental weakness in the STORJ system is that the token is not required for purchasing storage.
Timing
With many ICO ideas, the timing may be too late or too early. It’s important for the analyst to consider how much demand there is for the product in question. While the IPO boom funded a lot of great ideas that eventually did come to fruition, a good analyst would recognize when an idea is too early, too late, or just right.
Progress To Date
Some of the least compelling ICO propositions are those that claim their founders will achieve some far-off goal, sometime in the future, just so long as they have your cash with which to do it.
More interesting (usually) is the ICO that seeks to further some progress along the path to success, and which has a clearly-identified roadmap with achievable and reasonable milestones along the way. Founders who are already partially-invested in their products are generally more invested in their futures.
Community Support & Hype
Having a strong community is one of the fundamental building blocks of any strong blockchain project. It is important that the project demonstrates early on that it is able to generate and build a strong and empowered support base.
The ICO marketplace is becoming more crowded and more competitive. While in the past it was enough to merely announce an offering, today’s successful ICO’s work hard to build awareness and excitement around their offering.
Price & Token Distribution
One of the biggest factors weighing any analysis is price. The lower the price the more there is to gain. But too low of a price may result in an under capitalized project. It is therefore important to evaluate price relative to the individual project, its maturity and the market it is going after.
The total supply of tokens should also be justified by the needs of the project. Issuing a billion tokens for no reason will do nobody any good.
Communication
Communication is key. The success of a project is strongly tied to the project leaders’ ability to communicate their goals and achievements.
Things don’t always go as planned but addressing issues and keeping the community and investors in the loop can make or break a project.
Share this article
