Crypto Detective Exposes Scammer Behind OpenAI CTO & Bored Ape CEO SIM Swaps
On-chain detective ZachXBT identified a scammer who assisted in 17 SIM swap attacks.
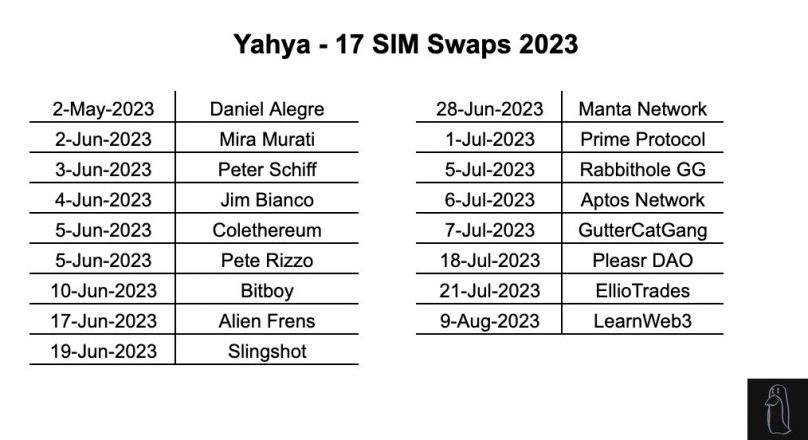
A new investigation by pseudonymous crypto detective ZachXBT has exposed the role of Canadian scammer Yahya in assisting in 17 SIM swap attacks that resulted in more than $4.5 million stolen in 2023.
In SIM swaps, hackers trick phone companies into moving a victim’s phone number onto a SIM card the hackers have. This lets the hackers get into all the victim’s accounts linked to their phone numbers.
According to the findings, Yahya participated in 17 SIM swaps this year, targeting victims including Yuga Labs CEO Daniel Alegre, OpenAI CTO Mira Murati, crypto influencer Bitboy, the Aptos Foundation, and PleasrDAO.
Yahya’s role was to conduct lookups on targets’ phone numbers and social media accounts using his access to data tools. This information was then used by the lead scammer Skenkir to carry out SIM swap attacks on victims in the US. As payment, Yahya received a percentage of the proceeds from each successful theft.
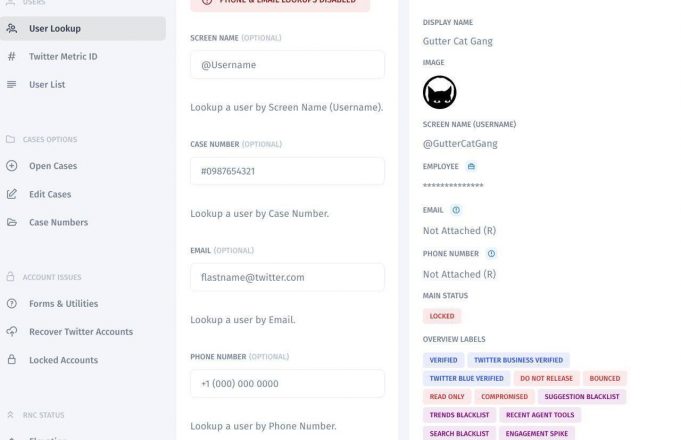
The investigation provides several examples of attacks in which Yahya participated. One is the July 2022 attack on the Gutter Cat Gang team, which resulted in over $720,000 in losses. Yahya received $250,000 for his contribution. Other victims named include crypto influencer Bitboy Crypto, who lost $950,000, and PleasrDAO member Jamis, whose attack resulted in $1.3 million stolen.
In total, Yahya’s wallet address received over 390 ETH ($720,000) from the 17 SIM swap attacks.
Earlier this year, ZachXBT reported that 54 high-profile victims were targeted in SIM swap attacks in 2023. In total, these victims lost over $13 million.